Add Linux computer to Windows domain
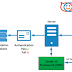
In this post we will see how to add a Linux machine to an Active Directory domain. The idea is that the authentication of the Linux machine is done using Kerberos.
The procedure to follow will be as follows:
Add Linux machine to Windows domain: Example data:
- Name of the Linux computer to add to the domain: CentOS8AD
- IP address of the domain controller (DC): 192.168.0.210, 192.168.0.253
- Name of the Active Directory domain: ITINFS.lab
Add Linux computer to domain Windows: TCP / IP configuration
When configuring the TCP / IP of the Linux computer, we must bear in mind that we must configure:
1) As the primary DNS server, the IP address of our Windows domain controller (DC).
2) As the search domain, we must configure the Active Directory domain name.
Viewing the content of the /etc/resolv.conf file, we can see the result:
[root @ CentOS8AD ~] # cat /etc/resolv.conf
# Generated by NetworkManager
search ITINFS.lab
nameserver 192.168.0.210
nameserver 192.168.0.253
Add Linux machine to domain Windows: Config NTP
All Windows or Linux computers added to an Active Directory domain require a domain controller (DC) to be configured as a time server.
On Windows computers that are added to an Active Directory domain, this configuration is done automatically.
If the computer that we are going to add to an Active Directory domain has a Linux operating system, we must perform the NTP configuration manually.
To do this, we will follow the following procedure:
We install the package:
yum install ntp -y
We make a backup copy of the original file, with the -a parameter, we copy the permissions.
cp -a /etc/ntp.conf /etc/ntp.conf.original
Edit the configuration file:
vi /etc/ntp.conf
We comment : #restrict default nomodify notrap nopeer noquery
We add: restrict default nomodify notrap nopeer noquery kod limited
We comment:
#server 0.centos.pool.ntp.org iburst
#server 1.centos.pool.ntp.org iburst
#server 2.centos .pool.ntp.org iburst
#server 3.centos.pool.ntp.org iburst
We add:
server 192.168.0.210 iburst
#Indicate the IP address of the DC.
We start the service and configure it to start automatically when starting the computer:
systemctl start ntpd
systemctl enable ntpd
Test:
ntpq -p
We will see how the domain controller (DC) appears.
Once the first steps have been made to join the linux computer to the Windows domain , we will proceed to restart the Linux client to apply the changes to the computer name.
Add Linux machine to domain Windows: Add
Once done we have to install samba and realm , the program that will make our work much easier
dnf install realmd sssd oddjob oddjob-mkhomedir adcli samba-common samba-common-tools krb5-workstation authselect-compat
[root@CentOS8AD ~]# dnf install realmd sssd oddjob oddjob-mkhomedir adcli samba-common samba-common-tools krb5-workstation authselect-compat
Last metadata expiration check made 0:16:02 ago, on Mon Mar 22 2021 16:36:43 EDT.
The package realmd-0.16.3-19.el8.x86_64 is already installed.
The sssd-2.3.0-9.el8.x86_64 package is already installed.
The oddjob-0.34.5-3.el8.x86_64 package is already installed.
The oddjob-mkhomedir-0.34.5-3.el8.x86_64 package is already installed.
The adcli-0.8.2-7.el8.x86_64 package is already installed.
The samba-common-4.12.3-12.el8.3.noarch package is already installed.
The authselect-compat-1.2.1-2.el8.x86_64 package is already installed.
Dependencies resolved.
=================================================================================================================================================================================================================
Architecture Package Repository Version Size.
=================================================================================================================================================================================================================
Installing:
krb5-workstation x86_64 1.18.2-5.el8 baseos 955 k
samba-common-tools x86_64 4.12.3-12.el8.3 baseos 484 k
Installing dependencies:
libkadm5 x86_64 1.18.2-5.el8 baseos 185 k
samba-libs x86_64 4.12.3-12.el8.3 baseos 188 k
Transaction Summary
=================================================================================================================================================================================================================
Install 4 Packages
Total discharge size: 1.8M
Installed Size: 5.0M
Do you agree [y / N] ?:
Once this is done we are going to inspect the domain we are going to join.
Sometimes the full domain name does not work and we have to use NETBIOS name or vice versa. In this case we see that it works with the full domain name, and not with the NETBIOS name:
[root@CentOS8AD ~]# realm discover ITINFS.lab
itinfs.lab
type: kerberos
realm-name: ITINFS.LAB
domain-name: itinfs.lab
configured: no
server-software: active-directory
client-software: sssd
required-package: oddjob
required-package: oddjob-mkhomedir
required-package: sssd
required-package: adcli
required-package: samba-common-tools
If DNS name resolution doesn't work (the previous step), you can always try resolving to netbios name.
In this case it would be:
[root@CentOS8AD ~]# realm discover ITINFS
Once we have verified that we have communication with it and that the program recognizes it correctly, we proceed to link it with realm
Now we are going to proceed to add the computer to the Active Directory domain with realm:
[root@CentOS8AD ~]# realm join -U Administrador itinfs.lab
Password for Administrator:
[root@CentOS8AD ~]#
the join command of realm allows you to join the computer to the specified domain .
-U Specifies the user to use to join the domain
We can check the list of realm commands from the official Red Hat documentation.
We check that we are in the domain:
[root@CentOS8AD ~]# realm list
itinfs.lab
type: kerberos
realm-name: ITINFS.LAB
domain-name: itinfs.lab
configured: kerberos-member
server-software: active-directory
client-software: sssd
required-package: oddjob
required-package: oddjob-mkhomedir
required-package: sssd
required-package: adcli
required-package: samba-common-tools
login-formats: %U@itinfs.lab
login-policy: allow-realm-logins
If we go to the domain we will also see in the list:
We restart the ssssd login agent service
[root@CentOS8AD
~]# systemctl restart sssd
[root@CentOS8AD
~]# systemctl status sssd
●
sssd.service - System Security Services Daemon
Loaded:
loaded (/usr/lib/systemd/system/sssd.service; enabled; vendor preset: enabled)
Active:
active (running) (thawing) since Mon 2021-03-22 17:09:43 EDT; 5s ago
Main
PID: 25552 (sssd)
Tasks:
5 (limit: 23663)
Memory:
41.0M
CGroup:
/system.slice/sssd.service
├─25552
/usr/sbin/sssd -i --logger=files
├─25554
/usr/libexec/sssd/sssd_be --domain implicit_files --uid 0 --gid 0
--logger=files
├─25555
/usr/libexec/sssd/sssd_be --domain itinfs.lab --uid 0 --gid 0 --logger=files
├─25556
/usr/libexec/sssd/sssd_nss --uid 0 --gid 0 --logger=files
└─25557
/usr/libexec/sssd/sssd_pam --uid 0 --gid 0 --logger=files
mar
22 17:09:42 CentOS8AD.itinfs.lab systemd[1]: sssd.service: Succeeded.
mar
22 17:09:42 CentOS8AD.itinfs.lab systemd[1]: Stopped System Security Services
Daemon.
mar
22 17:09:42 CentOS8AD.itinfs.lab systemd[1]: Starting System Security Services
Daemon...
mar
22 17:09:42 CentOS8AD.itinfs.lab sssd[25552]: Starting up
mar
22 17:09:42 CentOS8AD.itinfs.lab be[itinfs.lab][25555]: Starting up
mar
22 17:09:42 CentOS8AD.itinfs.lab be[implicit_files][25554]: Starting up
mar
22 17:09:43 CentOS8AD.itinfs.lab pam[25557]: Starting up
mar
22 17:09:43 CentOS8AD.itinfs.lab nss[25556]: Starting up
mar
22 17:09:43 CentOS8AD.itinfs.lab systemd[1]: Started System Security Services
Daemon.
[root@CentOS8AD
~]#
We enable the login agent:
[root@CentOS8AD
~]# sudo authselect select sssd with-mkhomedir
Profile
"sssd" was selected.
The
following nsswitch maps are overwritten by the profile:
-
passwd
-
group
-
netgroup
-
automount
-
services
Make
sure that SSSD service is configured and enabled. See SSSD documentation for
more information.
So that ssd can generate the home directories of the AD user, we will enable the mkhomedir function in sssd
We will make sure that the SSSD
agent starts during boot
[pcxlq@CentOS8AD ~]$ systemctl
status sssd
●
sssd.service - System Security Services Daemon
Loaded: loaded (/usr/lib/systemd/system/sssd.service; enabled; vendor
preset: enabled)
Active: active (running) since Mon 2021-03-22 18:08:53 EDT; 7min ago
Main
PID: 733 (sssd)
Tasks: 5 (limit: 23663)
Memory: 66.6M
CGroup: /system.slice/sssd.service
├─733 /usr/sbin/sssd -i --logger=files
├─753 /usr/libexec/sssd/sssd_be --domain
implicit_files --uid 0 --gid 0 --logger=files
├─754 /usr/libexec/sssd/sssd_be --domain itinfs.lab
--uid 0 --gid 0 --logger=files
├─759 /usr/libexec/sssd/sssd_nss --uid 0
--gid 0 --logger=files
└─760 /usr/libexec/sssd/sssd_pam --uid 0 --gid 0 --logger=files
mar
22 18:08:52 CentOS8AD.itinfs.lab be[itinfs.lab][754]: Starting up
mar
22 18:08:53 CentOS8AD.itinfs.lab nss[759]: Starting up
mar
22 18:08:53 CentOS8AD.itinfs.lab pam[760]: Starting up
mar
22 18:08:53 CentOS8AD.itinfs.lab systemd[1]: Started System Security Services
Daemon.
mar
22 18:08:57 CentOS8AD.itinfs.lab be[itinfs.lab][754]: Backend is online
mar
22 18:08:58 CentOS8AD.itinfs.lab adcli[1137]: GSSAPI client step
[
pcxlq@CentOS8AD ~] $
Make
sure that SSSD service is configured and enabled. See SSSD documentation for
more information.
-
with-mkhomedir is selected, make sure pam_oddjob_mkhomedir module
is present and oddjobd service is enabled and active
- systemctl enable --now oddjobd.service
Make
sure that SSSD service is configured and enabled. See SSSD documentation for
more information.
We make sure that the function
starts the oddjobd.service module , so that mkdirhome works :
[root@CentOS8AD
~]# systemctl enable --now
oddjobd.service
[pcxlq@CentOS8AD
~]$ systemctl status oddjobd.service
●
oddjobd.service - privileged operations for unprivileged applications
Loaded:
loaded (/usr/lib/systemd/system/oddjobd.service; enabled; vendor preset:
disabled)
Active:
active (running) since Mon 2021-03-22 18:08:54 EDT; 8min ago
Main
PID: 777 (oddjobd)
Tasks:
1 (limit: 23663)
Memory:
1.4M
CGroup:
/system.slice/oddjobd.service
└─777
/usr/sbin/oddjobd -n -p /var/run/oddjobd.pid -t 300
mar
22 18:08:54 CentOS8AD.itinfs.lab systemd[1]: Started privileged operations for
unprivileged applications.
[ pcxlq@ CentOS8AD ~] $
Login using domain name:
PS
C:\Users\gshr> ssh itinfs.lab\gshr@192.168.0.42
itinfs.lab\gshr@192.168.0.42's
password:
Activate
the web console with: systemctl enable --now cockpit.socket
Last login: Mon Mar 22 19:38:38 2021 from 192.168.0.26
From the file " /etc/sssd/sssd.conf " we can change certain behaviors of the integration as if it is necessary to use FQDN, how the home directories are generated, etc ...
[root@CentOS8AD
~]# cat /etc/sssd/sssd.conf
[sssd]
domains
= itinfs.lab
config_file_version
= 2
services
= nss, pam
[domain/itinfs.lab]
ad_domain
= itinfs.lab
krb5_realm
= ITINFS.LAB
realmd_tags
= manages-system joined-with-adcli
cache_credentials
= True
id_provider
= ad
krb5_store_password_if_offline
= True
default_shell
= /bin/bash
ldap_id_mapping
= True
use_fully_qualified_names
= True
fallback_homedir
= /home/%u@%d
access_provider
= ad
We are going
to change the mandatory use of FQDN, for this we will change the Boolean to
false :
use_fully_qualified_names
= False
After each
change in the agent we must restart the sssd service for the changes to take
effect
From the
client we can limit which users or groups can enter the machine
We are going
to allow only Paco to access the machine ( Paco belongs to " group6 "):
[root@CentOS8AD ~]# realm
permit paco@itinfs.lab
[root@CentOS8AD ~]#
realm permit -g grupo6
We show how
the configuration of the sssd.conf file has been :
[root@CentOS8AD
~]# cat /etc/sssd/sssd.conf
[sssd]
domains
= itinfs.lab
config_file_version
= 2
services
= nss, pam
[domain/itinfs.lab]
ad_domain
= itinfs.lab
krb5_realm
= ITINFS.LAB
realmd_tags
= manages-system joined-with-adcli
cache_credentials
= True
id_provider
= ad
krb5_store_password_if_offline
= True
default_shell
= /bin/bash
ldap_id_mapping
= True
use_fully_qualified_names
= True
fallback_homedir
= /home/%u@%d
access_provider
= simple
simple_allow_users
= paco
simple_allow_groups
= grupo6
As we can
see, every change with the realm affects the sssd.conf, and therefore we must
restart the service to apply changes
Change the
shell of AD users
For this we will modify the file "/etc/sssd/sss.conf" and we will change the following line
default_shell
= /bin/sh
Remember
that after each change you have to restart the sssd
service
Adding AD
domain groups to /etc/sudoers
To do this, you would need to add an entry to
the /etc/sudoers file. /etc/sudoers gives listed users or groups the ability to
execute commands while having the privileges of the root user.
Editing /etc/sudoers
To edit /etc/sudoers safely, make sure to use the visudo
utility. This application will do a sanity check on your changes to /etc/sudoers before putting them into
production.
visudo uses
vi as its editor.
Adding the
following entry to /etc/sudoers
would allow you to give full sudo permissions to an AD group named ITadmins:
%ITINFS.LAB\\ITadmins ALL=(ALL) ALL
Since various AD group have spaces in the names, you'll have to get away from the spaces utilizing backslashes. For instance. adding the accompanying section /etc/sudoers would permit you to give full sudo permissions to an AD group named Group Name With Spaces:
%ITINFS.LAB\\Group\ Name\ With\ Spaces ALL=(ALL) ALL
And that's it, we've just seen how to join linux to active directory ; through realmd we can make the union of linux with a Windows domain , also working with the sssd agent and various options










Post a Comment